Inspecting Azure VMware Solution traffic with Network Virtual Appliance in Azure vNet
By: Trevor Davis, Azure Global Blackbelt - Azure VMware Solution - @vTrevorDavis
There are situations when the desire is to route all outbound traffic from Azure VMware Solution through a Network Virtual Appliance (NVA) which sits in an Azure Virtual Network. Here is how you would do that.
First read through my colleague Jorge Cortes’ great post which was the impetus for this article. I will not cover the detail Jorge does, and understanding his article is key to understand what is outlined here.
Jorge shows how to route all Internet bound traffic from Azure Virtual Networks or connected on-premises sites through a NVA in an Azure Virtual Network using Azure Virtual WAN. After reading Jorge’s post we did some testing and put Azure VMware Solution into the mix. Below are the results of our testing and how to add Azure VMware Solution to the design.
Quick summary of Jorge’s article.
- Deploy a network virtual appliance which can advertise a default route into an Azure Virtual Network.
- Build an IPsec tunnel from the NVA to Azure Virtual WAN
- Relay the default route coming from the NVA to some/all the spokes hanging off Azure Virtual WAN.
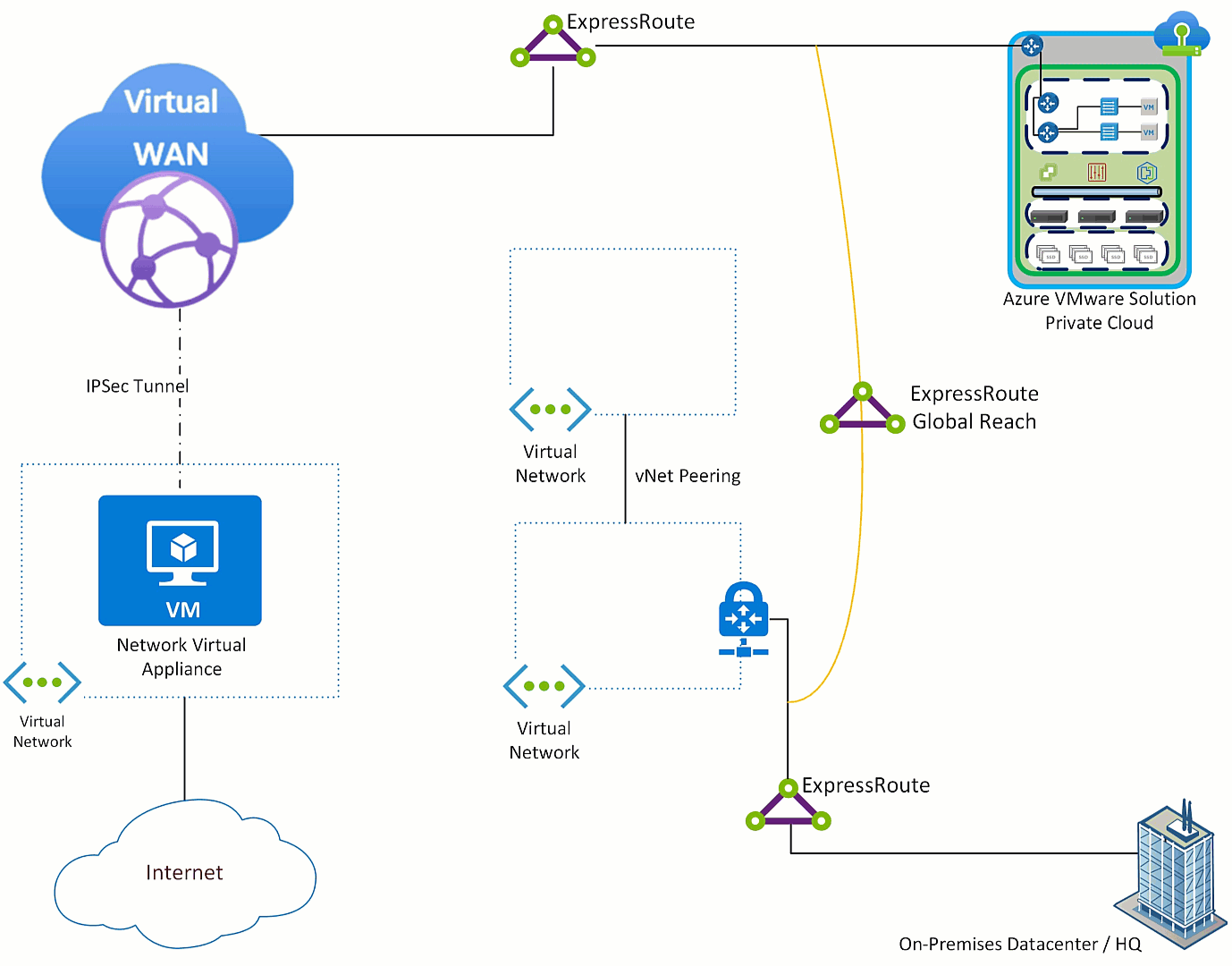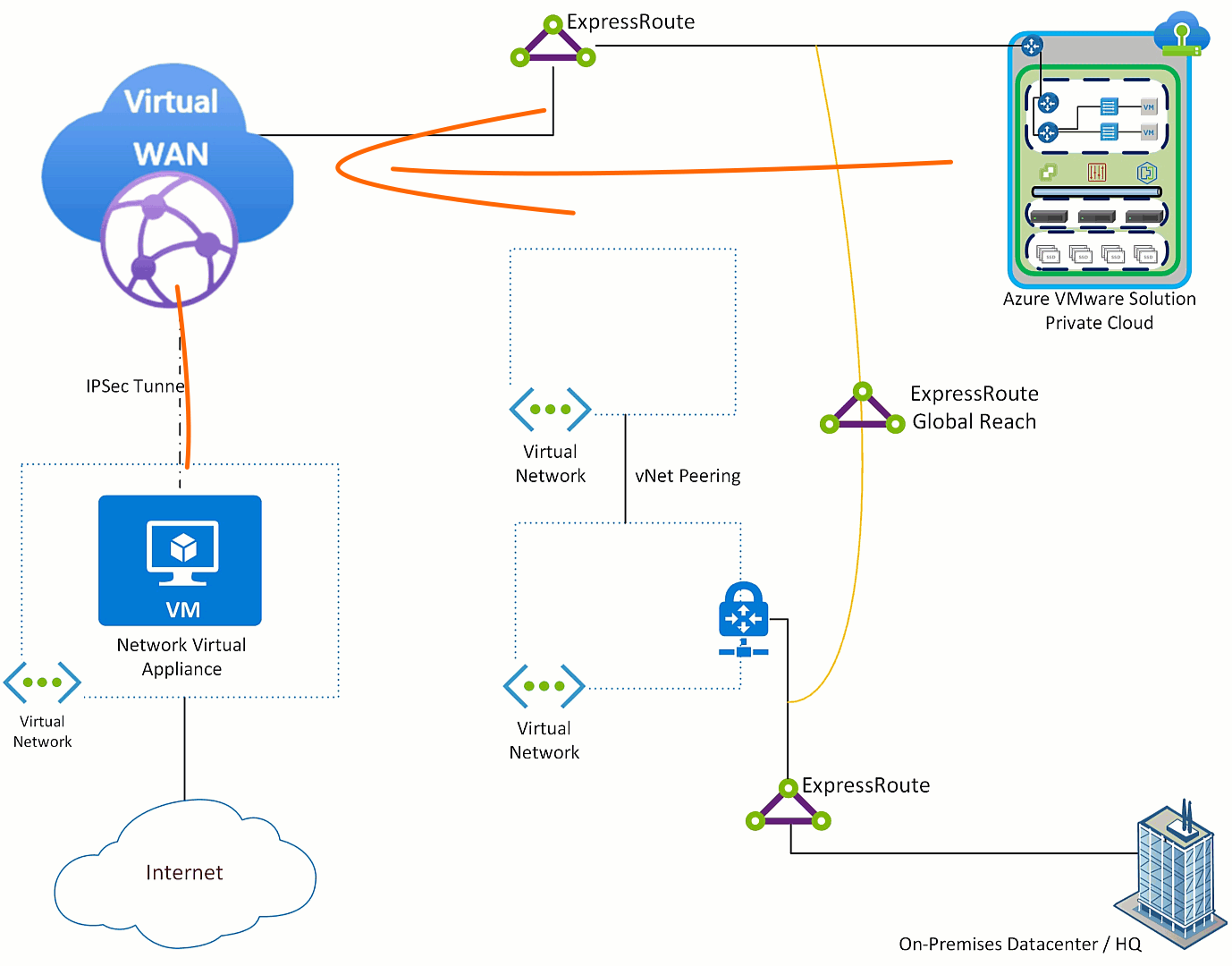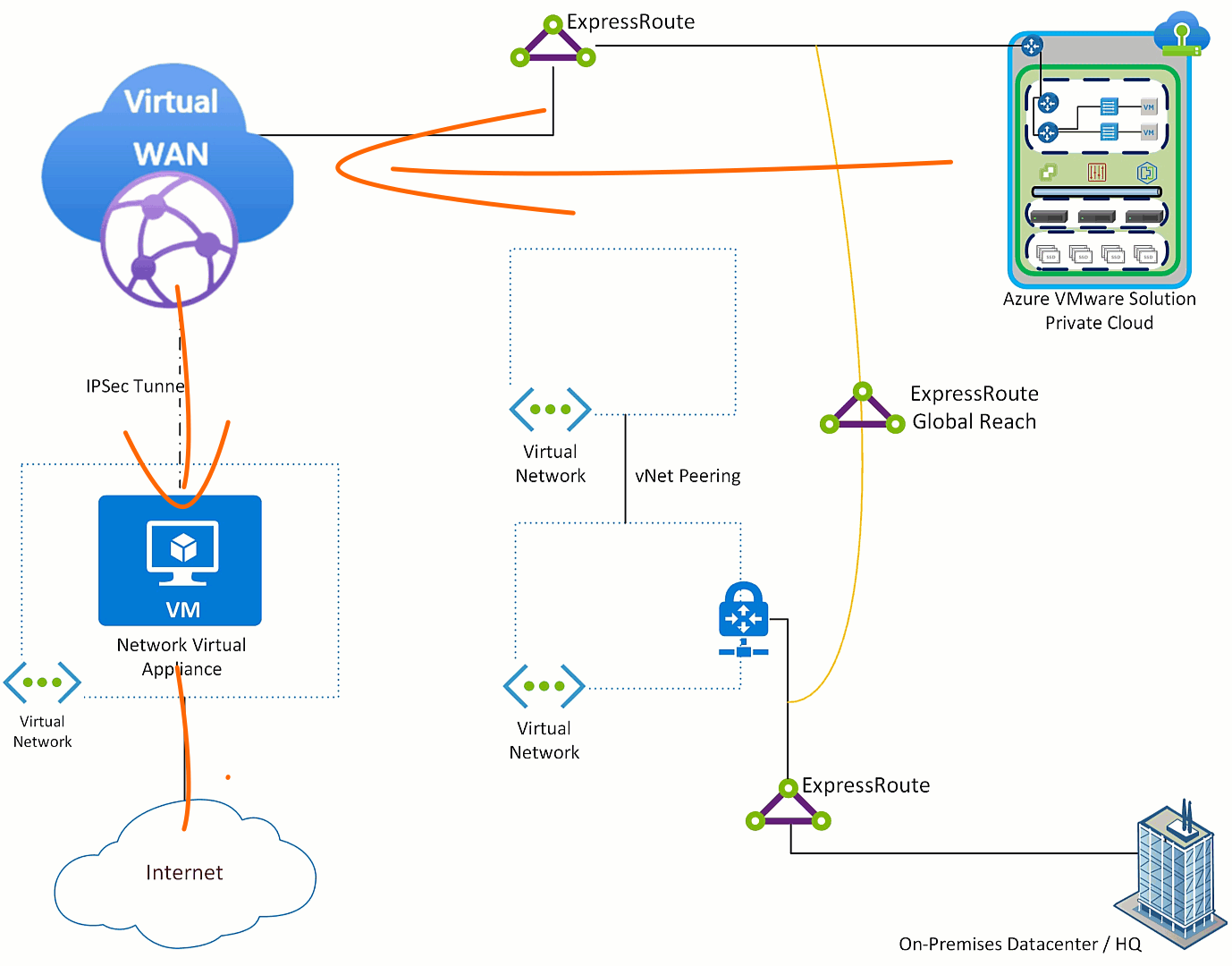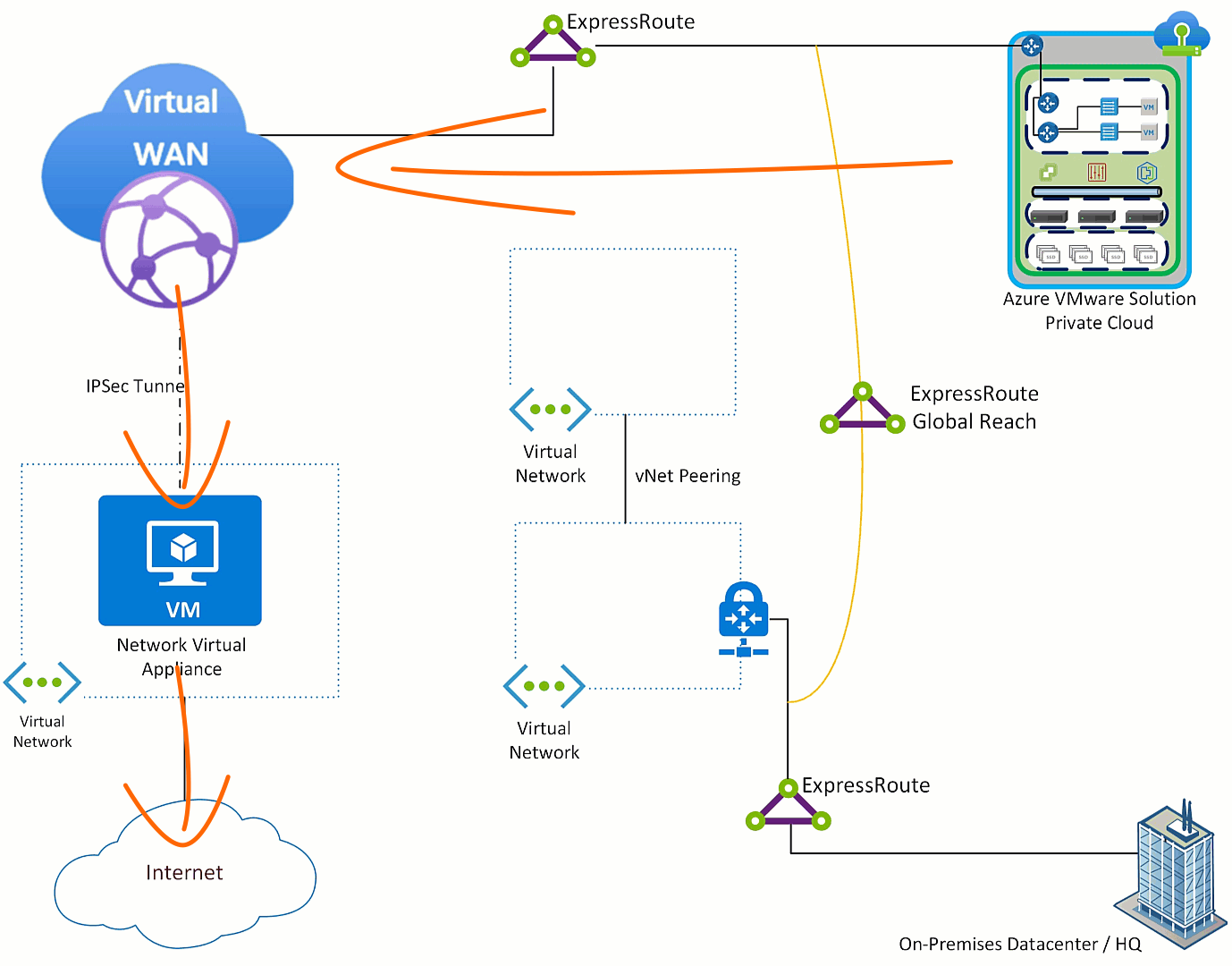
Now, we introduce Azure VMware Solution.
In the graphic below you see that Azure VMware Solution’s ExpressRoute terminated to Azure Virtual WAN and to the on-premises ExpressRoute via ExpressRoute Global Reach. Those connections allow Azure VMware Solution to communicate with Azure Virtual Networks and resources, in addition to the on-premises environment.
First step to get Azure VMware Solution sending Internet destined traffic to the NVA is to get Azure VMware Solution a default route advertisement. The NVA needs to have the ability to advertise a default route (this feature is table stakes), Azure Virtual WAN will learn that route and relay it to the ExpressRoute which connects Azure VMware Solution.
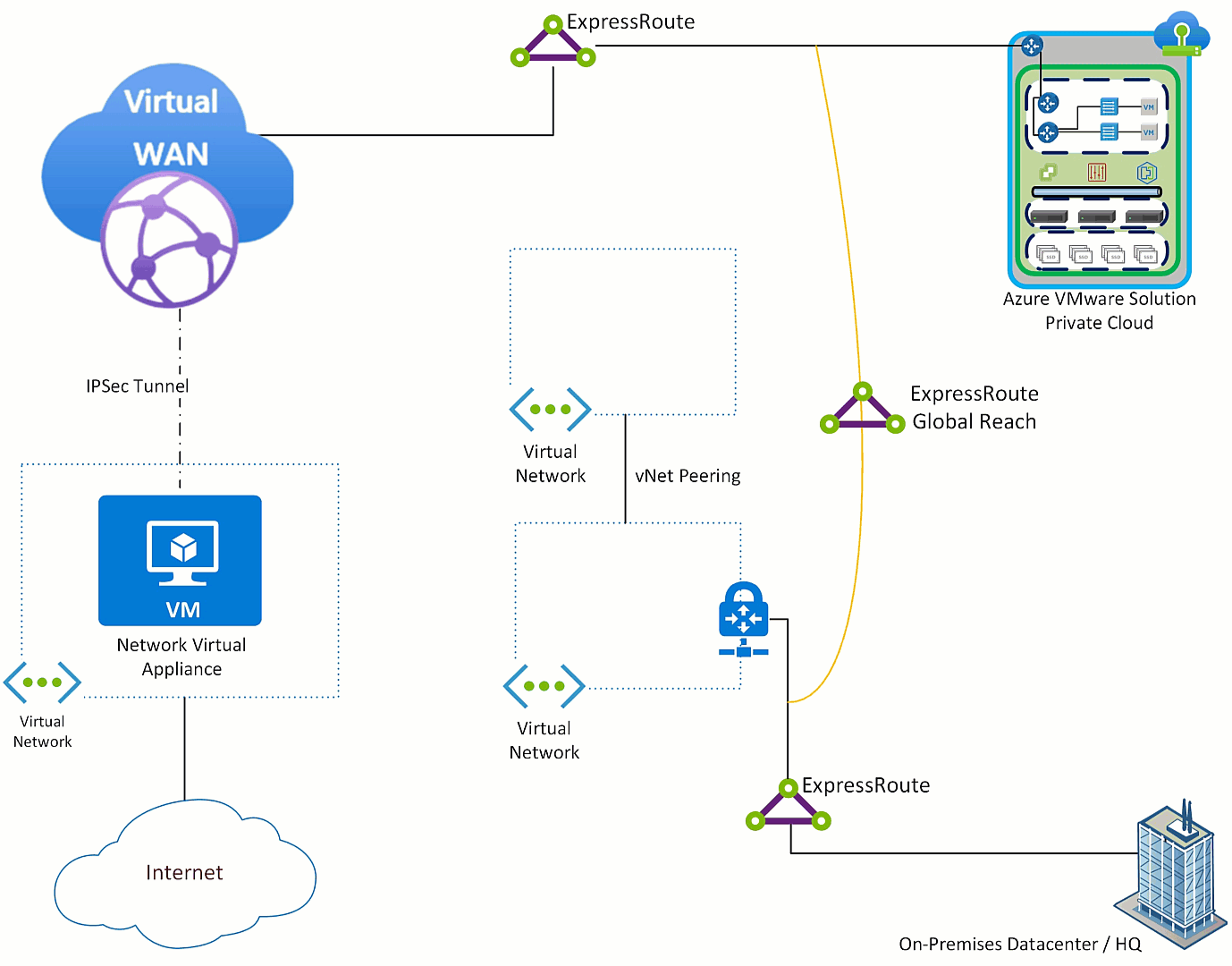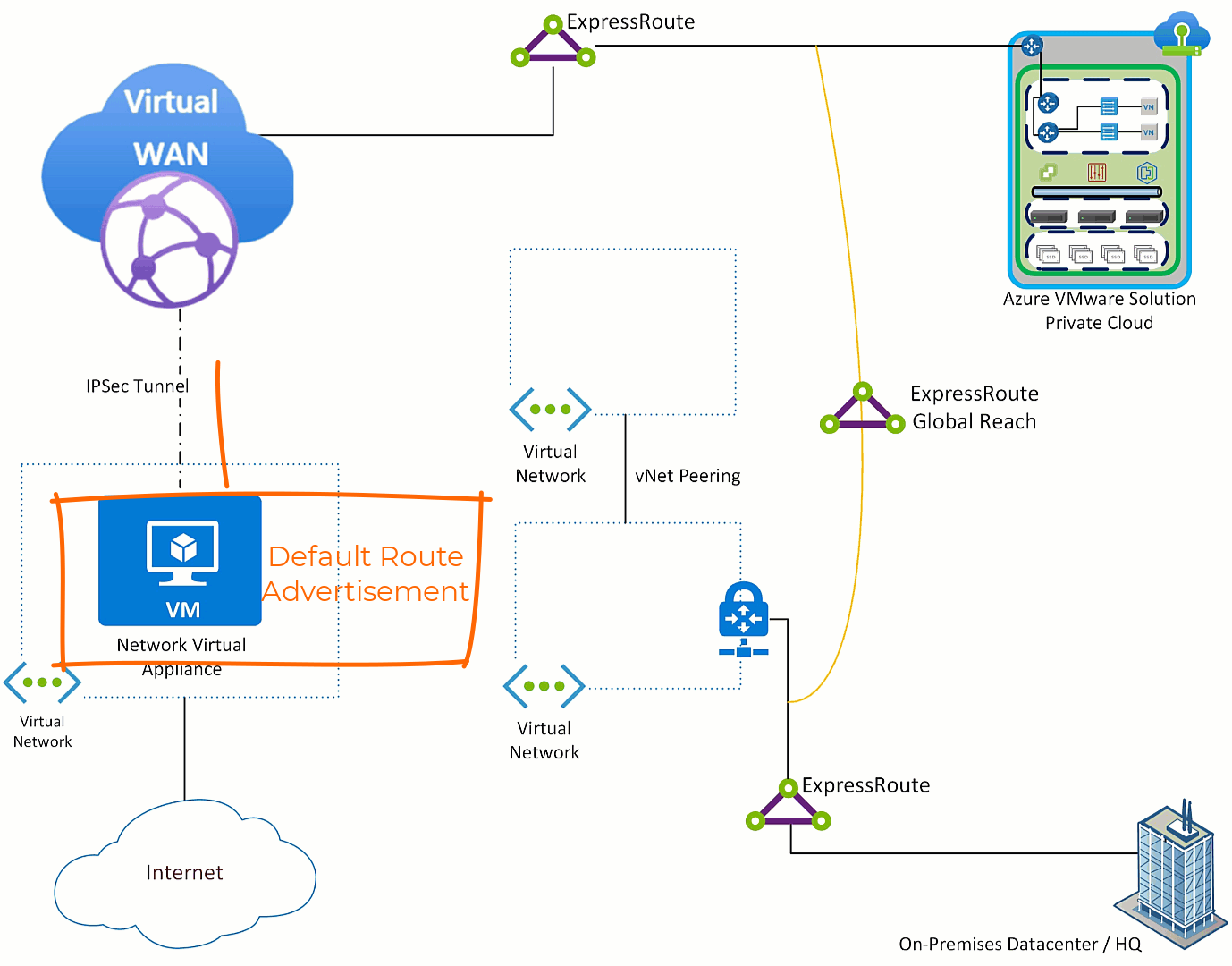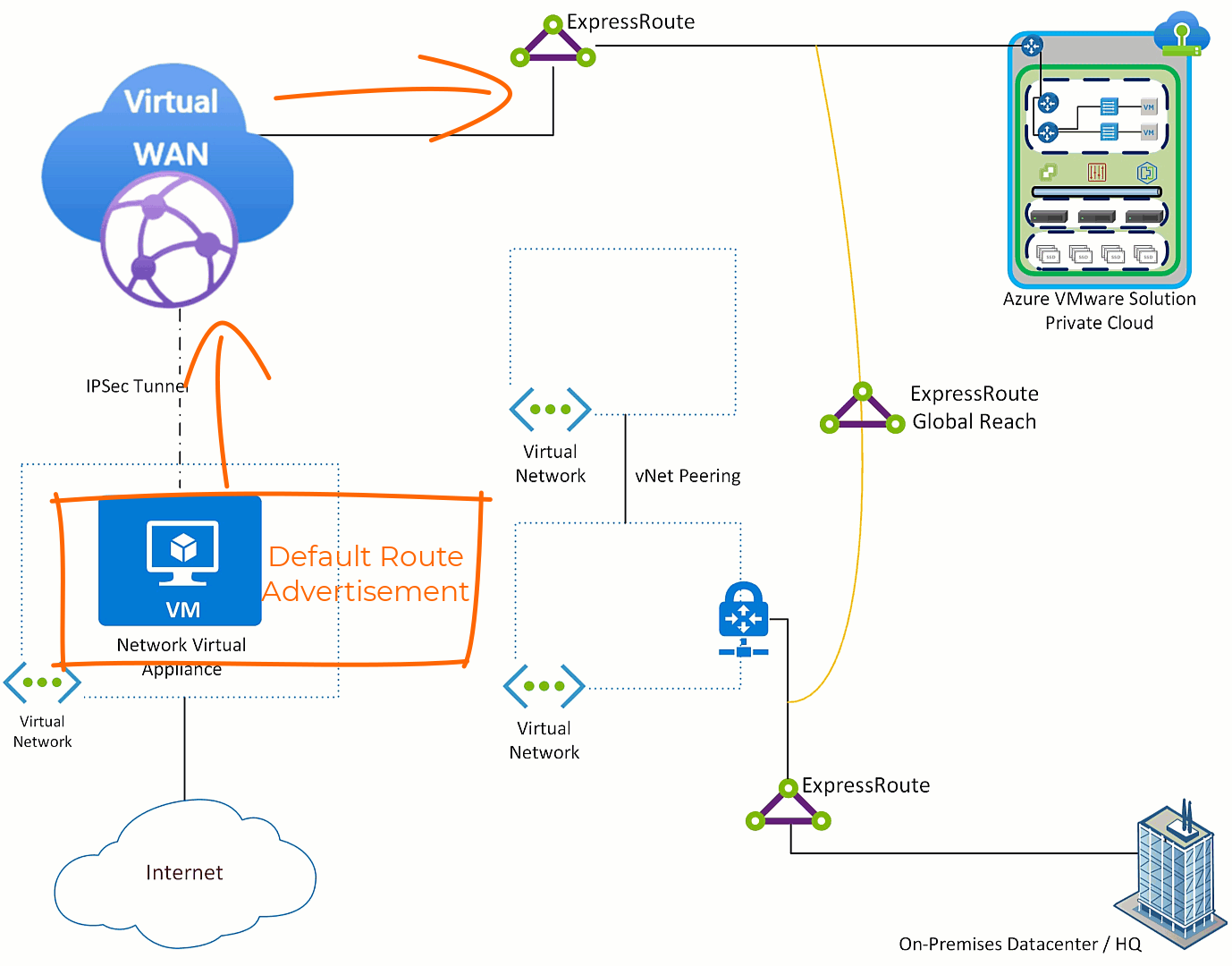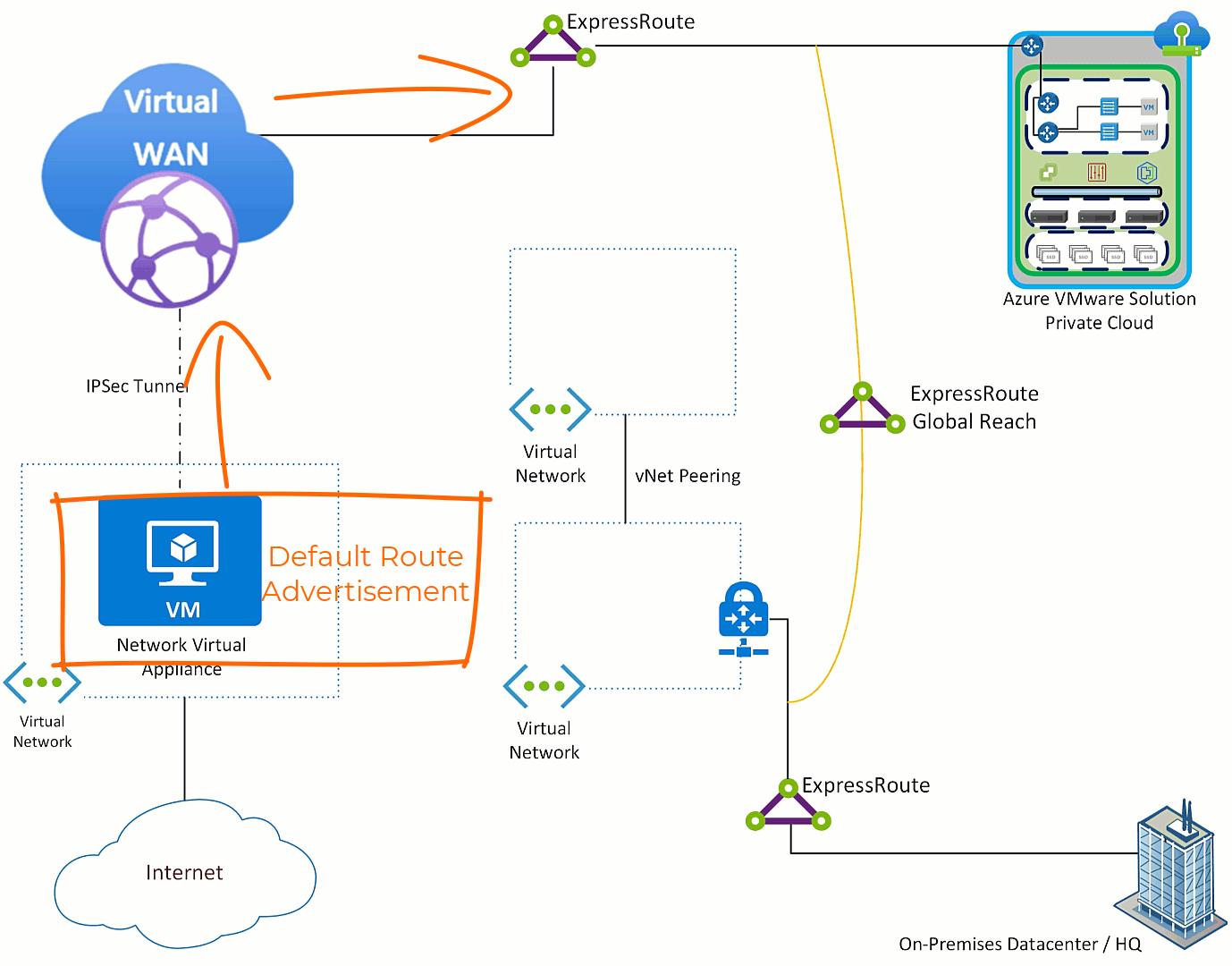
The default route is received by Azure VMware Solution, all Azure Virtual Networks and on-premises environment(s). This occurs because as the default route is sent across the ExpressRoute to Azure VMware Solution it also “leaks” to the ExpressRoute Global Reach connection and then to all things connected to the on-premises ExpressRoute.
Often customers are in a migration from the hub and spoke model to the Azure Virtual WAN network model and do not want hub and spoke virtual networks to exit through the NVA. Also, many times traffic coming from on-premises will not use Azure as the default route to the Internet. So, how is that addressed?
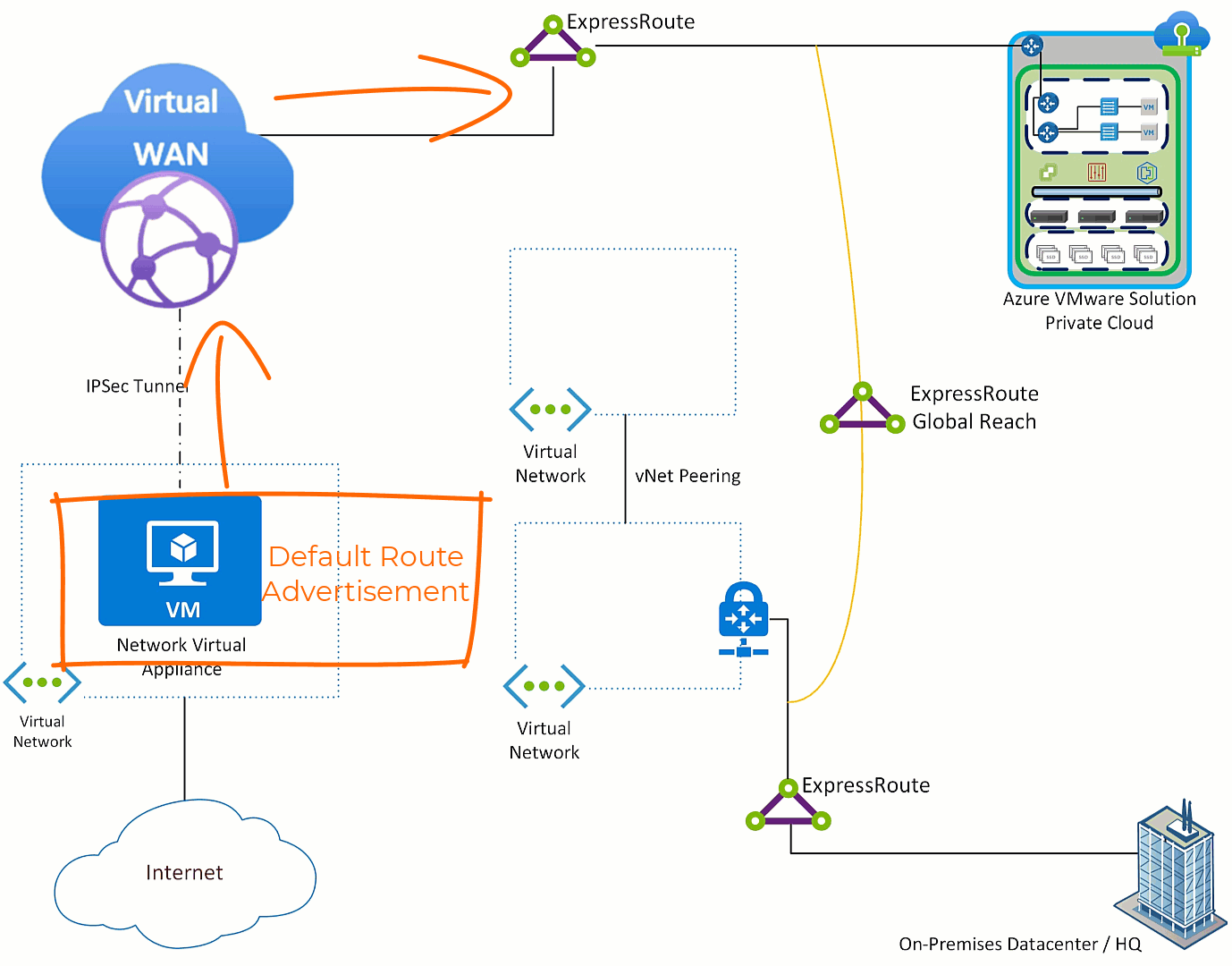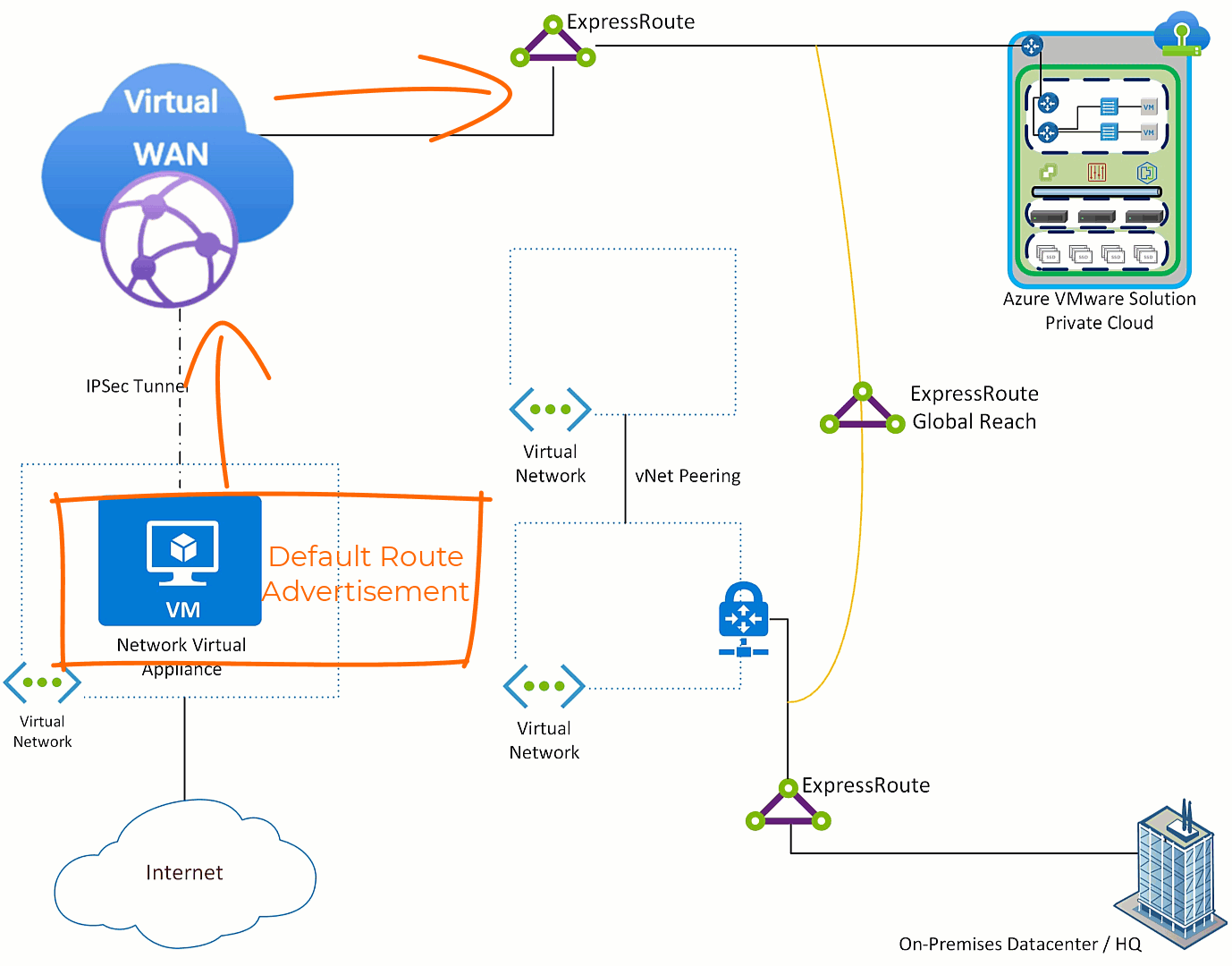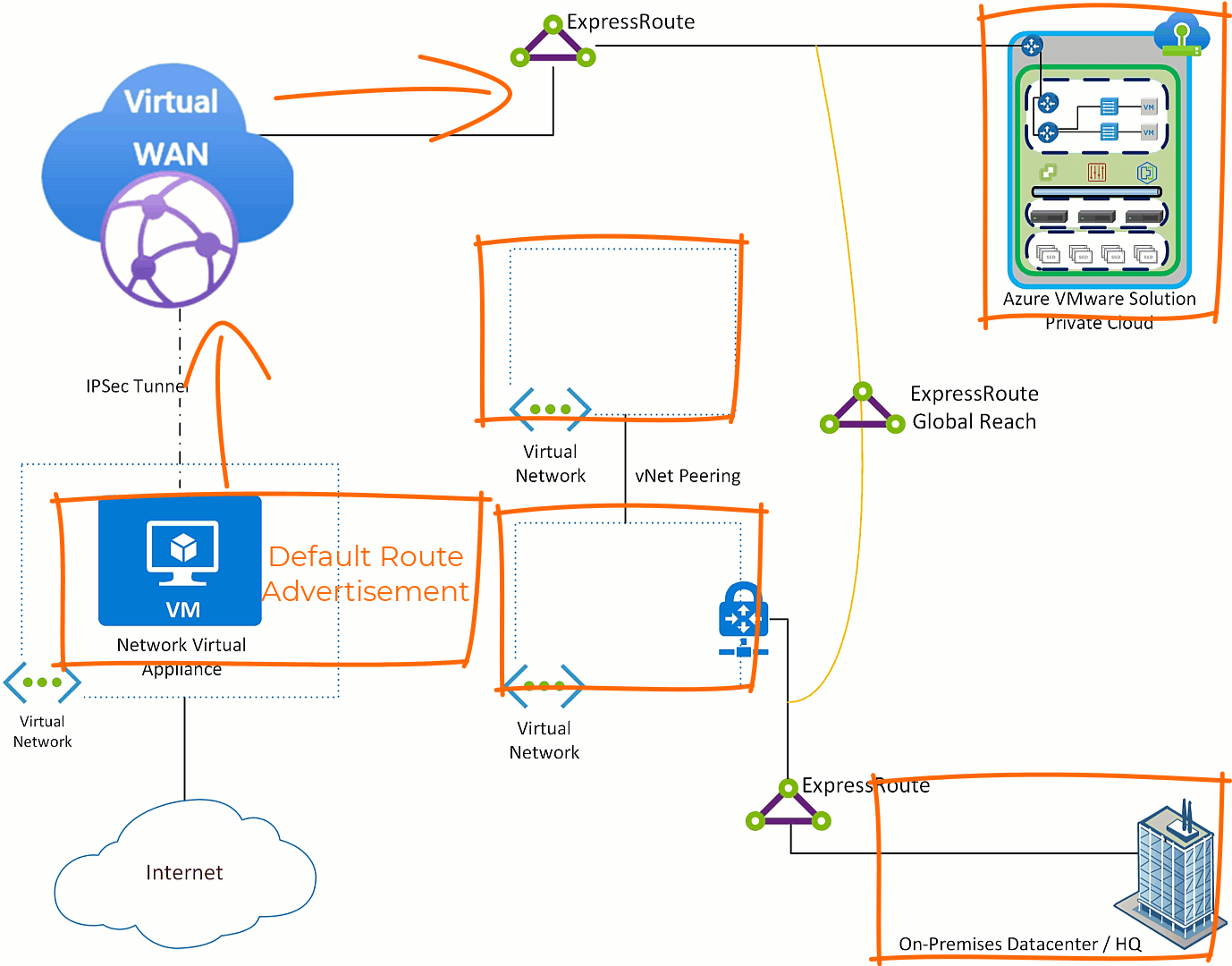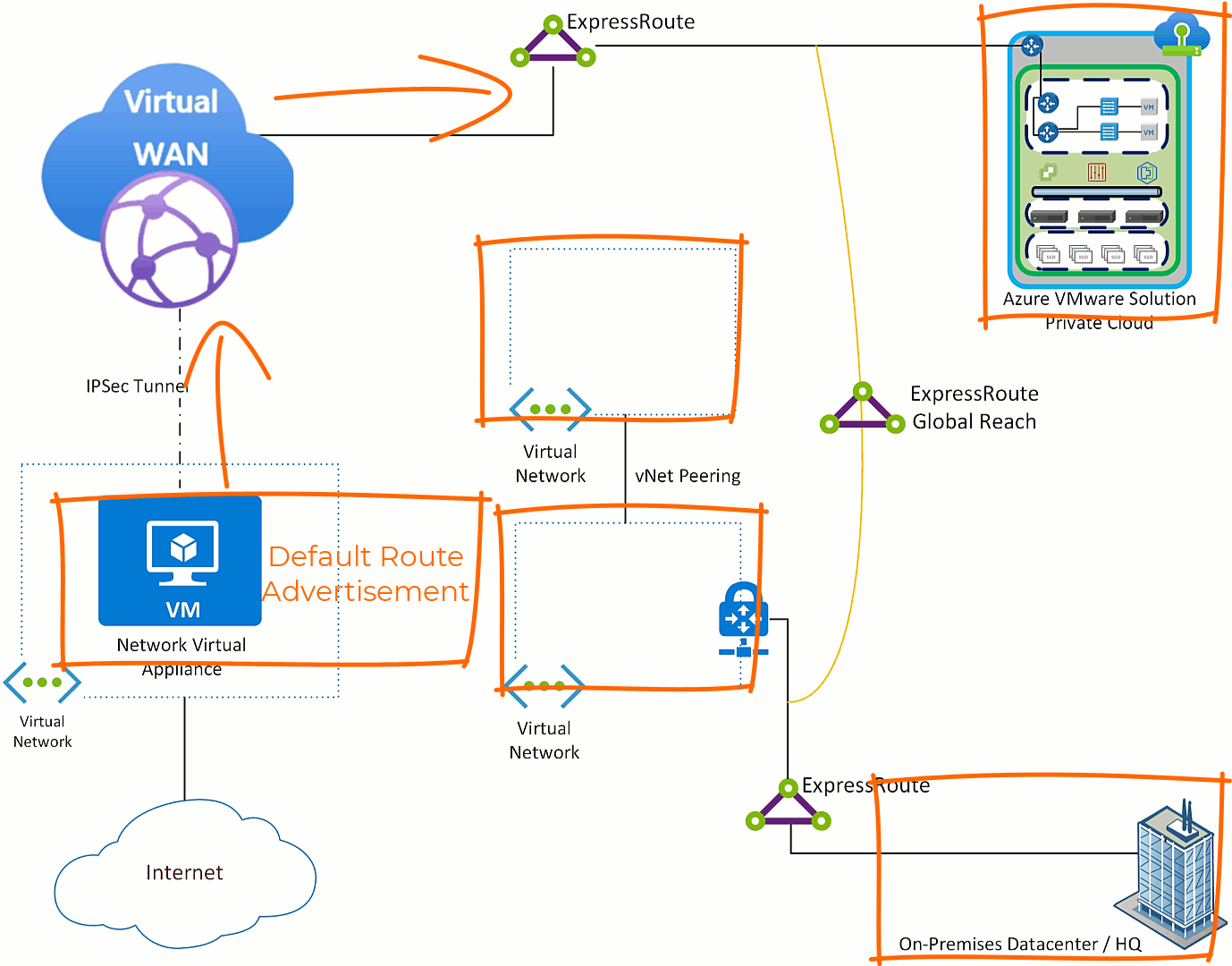
Do nothing with Azure VMware Solution, all traffic will exit via the NVA which is the desired outcome. Then on any Virtual Networks which you do not want to use the NVA, put a user defined route pointing the default route to “Internet”. Then in the on-premises environment filter the default route on the edge device where the ExpressRoute terminates.
After applying those the configuration items, the impact is that while is Azure VMware Solution is the only component which sends it’s Internet destined traffic to the NVA.